“The cyber threat has eclipsed the threat from physical terrorism.”
That statement reportedly came from Matthew Travis, a deputy undersecretary at Homeland Security during an event on the seventeenth anniversary of the September 11 terrorist attack. Days earlier, Secretary of Homeland Security Kirstjen Nielsen made the same point to college students, stating that her agency “was founded 15 years ago to prevent another 9/11” and that she believes “an attack of that magnitude is now more likely to reach us online than on an airplane.”
One glimpse at today’s headlines and it’s easy to see that advanced persistent cyber threats are very real and not going away.
“Not only do adversaries have knowledge of the vulnerabilities within systems and platforms across distributed networks,” said Deon Viergutz, vice president of Lockheed Martin Cyber Solutions, “they are targeting supply chains and they are keeping up with the rapid advances in technology, using automation and artificial intelligence to accelerate development of covert, persistent attacks that employ techniques such as steganography, cryptography, and reverse engineering, for example.”
So, if this is the new normal, how do we address it?
Understanding Vulnerabilities
For decades, the aerospace and defense industry has traditionally focused its attention on IT networks. Nowadays, weapon systems that used to be somewhat isolated from information networks now have countless numbers of touchpoints – for example interfaces to diagnostic equipment and mission planning data – that provide avenues to deliver malicious cyber agents to the weapon system.
Furthermore, nearly all operational platforms were designed, built, and deployed without a cyber contested environment in mind and hence do not have built-in defenses to these threats. Whereas ships run critical cabling port and starboard, high and low to be resilient to weapon strikes, typically there are not similar resiliency mechanisms designed into the information systems on the ship or other platforms. The risk is amplified by wide-use of common commercial software and hardware across platforms.
It is not an unreasonable question to ask – how many of our legacy systems are truly ready and resilient enough to function in a contested cyber environment?
“We know that discovering cyber vulnerabilities and deploying their remediation on standard corporate networks presents numerous complications,” said Viergutz. “But for military systems, cyber defense assumes a whole other set of challenges that cyber engineers must consider – 1. identifying mission threats; and 2. maintaining mission platform cyber resiliency.”
The concept of cyber resiliency can mean multiple things to different people. However, a common definition for “cyber resiliency” is the ability of a system to continue to operate in a degraded mode during an active cyber-attack and have a path to recover to full capability within deployed operations and maintenance channels. Lockheed Martin Fellow and cyber resiliency expert Patrick Lardieri likens the concept to the human body.
“If your skin, soap and water, and ultraviolet sterilization were the only defenses that you had against microbiological organisms that want to attack, you wouldn’t be around that long,” said Lardieri. “It’s unlikely that those protection mechanisms alone can fully prevent any intrusion. In fact, a huge part of your ability to fend off disease is your active immune system that’s fighting these bugs 24/7, seven days a week, your entire life.”
Cyber-attacks on a military system are no different. Without the proper protections built in, adversaries have an easier time to deny operations of critical parts of the system, overload networks, spoof messages, or take the system down entirely once they find one-way to circumvent cybersecurity protections.
Keys to Cyber Resiliency
“It’s a systems-engineering problem,” said Lardieri about designing a system to be cyber resilient. “In the event a cyber-attack penetrates your defenses, what kind of design features, manufacturing processes, supply chain control, and implemented functions and capabilities do you need so that [the attack] doesn’t totally disable the system for an indeterminate period of time and destroy the warfighter’s ability to meet their mission.”
Lardieri suggests there are four keys that systems-engineers must bear in mind when building in resiliency.
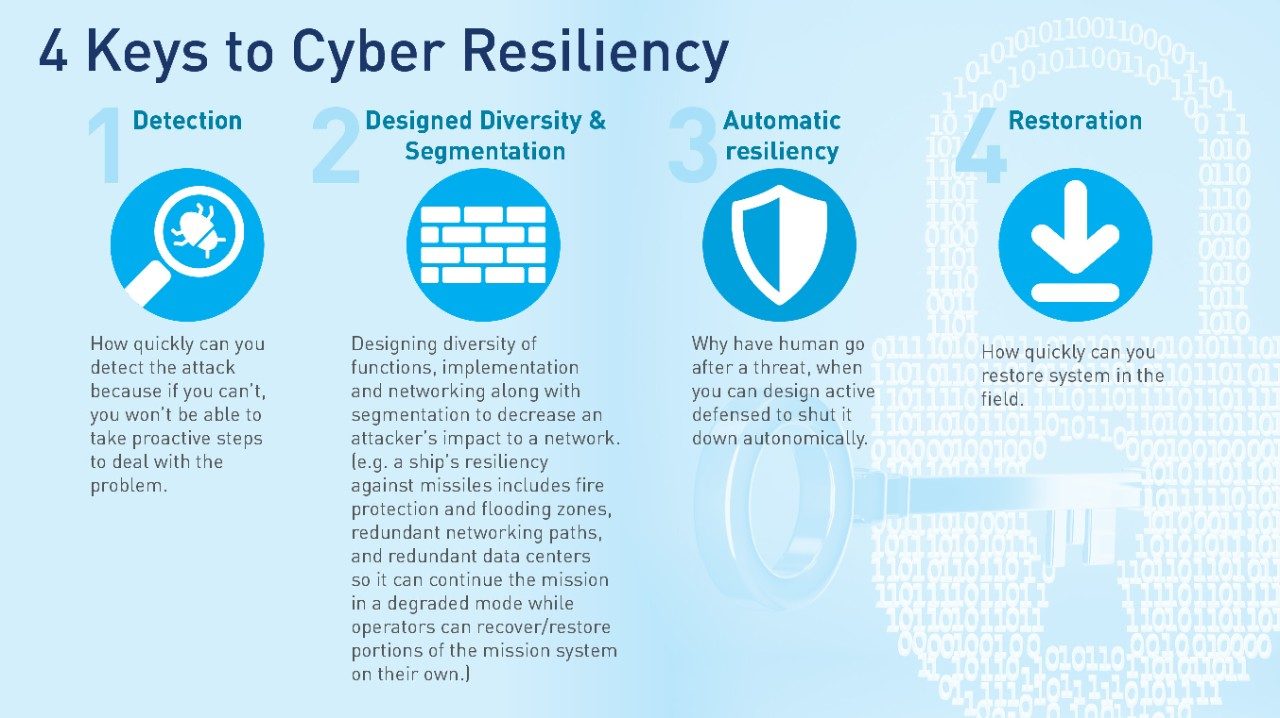
“In every one of these areas, you need a mix of software, hardware and human operations that need to be designed in concert,” said Lardieri. “Some will be commercial solutions, and some will be custom built – that’s what it takes to make a system resilient.”
The challenge is developing a realistic threat model that depicts specific attacks and their impacts on the system and mission. Lockheed Martin co-developed a cyber table top (CTT) process with the U.S. Naval Air Systems Command (NAVAIR) to address this need.
“We’ve seen success in teams using this process in the early part of the design phase,” said Lardieri. “The CTT process is so effective because it’s educational. Regardless of their cyber expertise, it helps people understand what the threats are and turn them into engineering problems they can solve. And as a result, they can see the art of the possible and where to focus their cyber resiliency design activities.”
A cyber table top exercise consists of four phases.
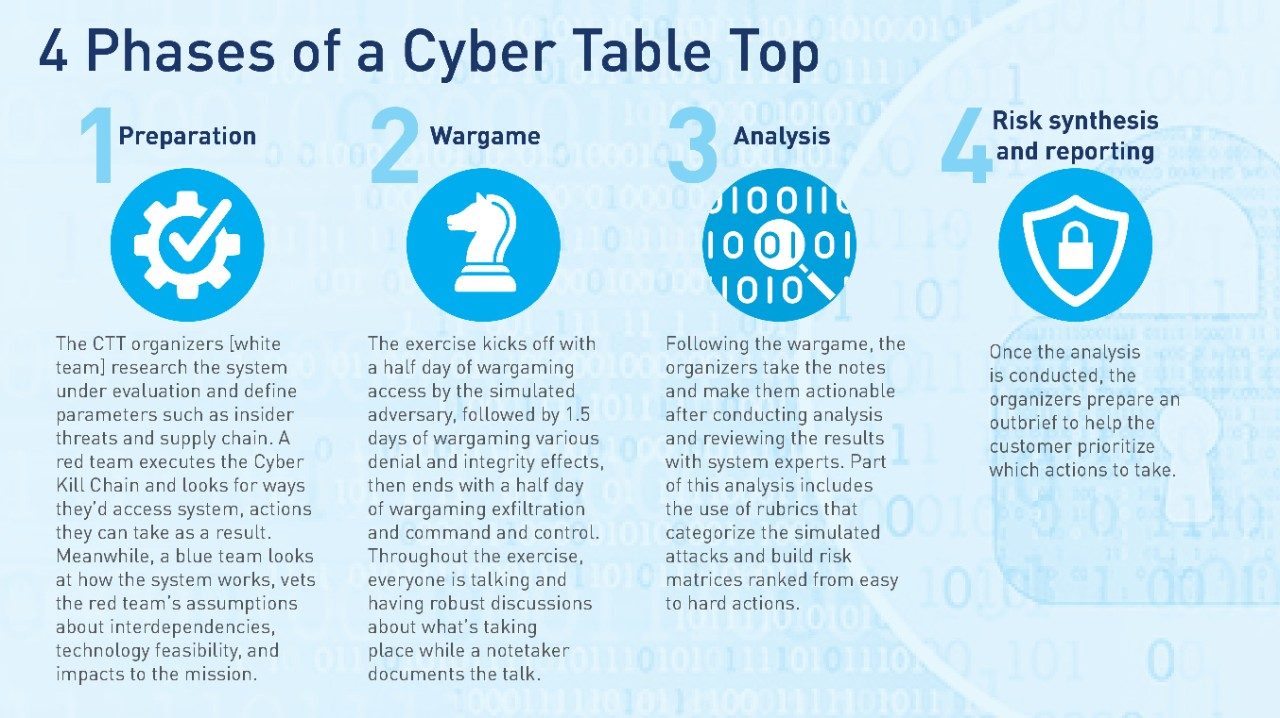
Ultimately, the CTT helps the recipient group drive how to fix vulnerabilities within their system.
“I often hear ‘I get it’ after we present them with the final report,” said Lardieri. “The end result provides a concrete set of problems to solve – it’s no longer just a spooky cyber problem.”
Going Beyond Compliance
The cybersecurity problems we so often hear about certainly are spooky enough that the U.S. government and its allies are increasing their demand for solutions to this problem. That’s why you’ll find more cyber-related sections in the recent National Defense Authorization Act than previous NDAAs.
Lardieri says to meet the evolving cyber threat, organizations must double-down on building in resiliency at the on-set of a system’s development rather than rely on the bolt-on approach that just doesn’t cut it anymore in today’s age.
“Cybersecurity needs to be part of the process and it needs to go beyond compliance,” explained Lardieri. “Through efforts like the National Cyber Range and classified efforts underway at Lockheed Martin, we have the potential to transform the engineering culture and make significant impact on national security.”




